Onboarding MacOS devices to Purview Using Intune
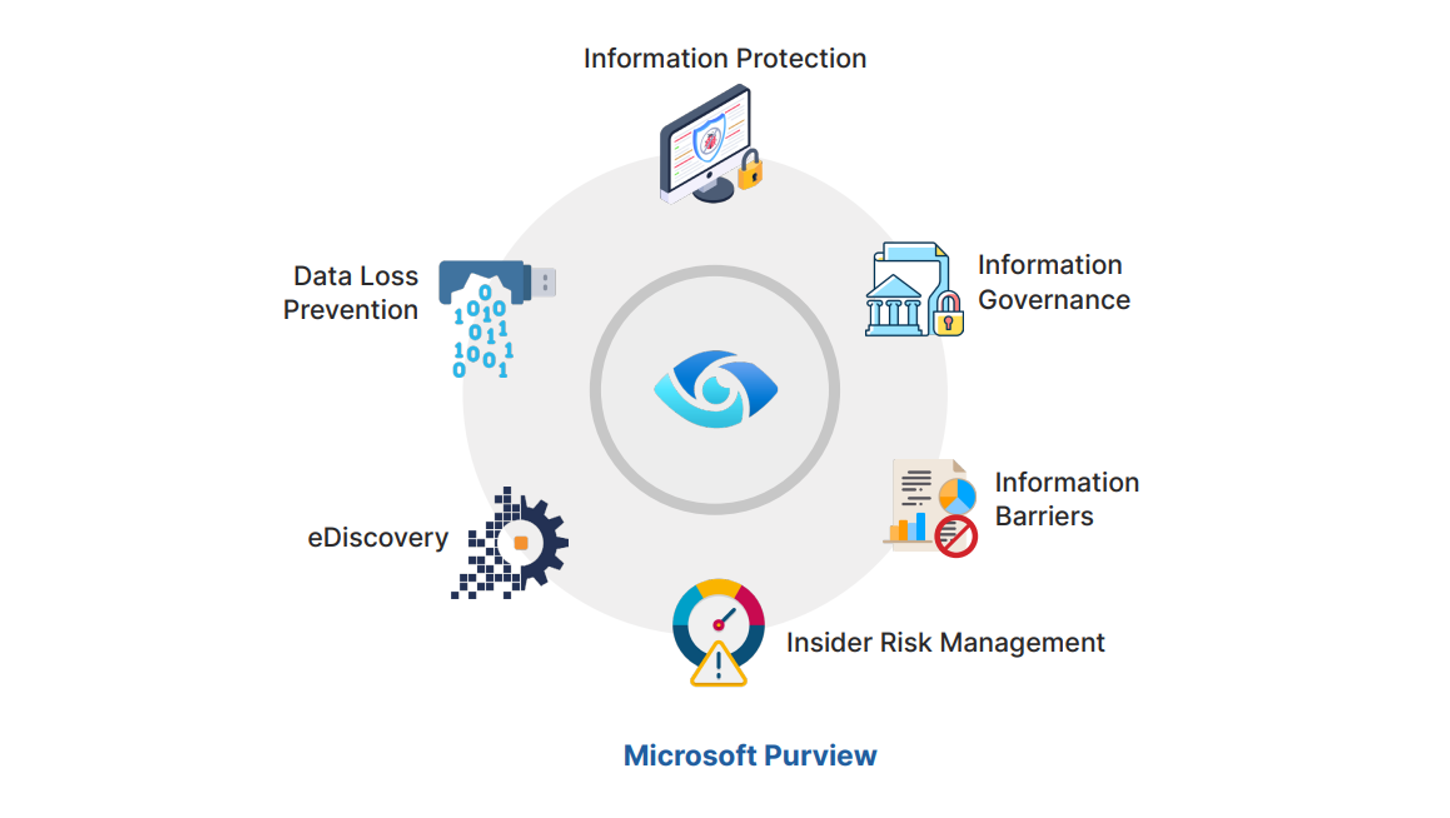
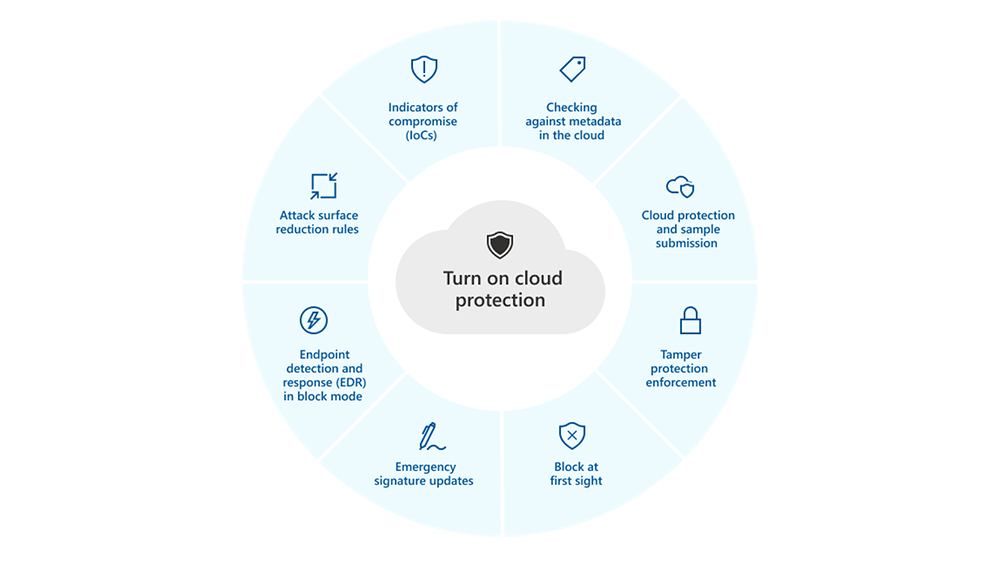
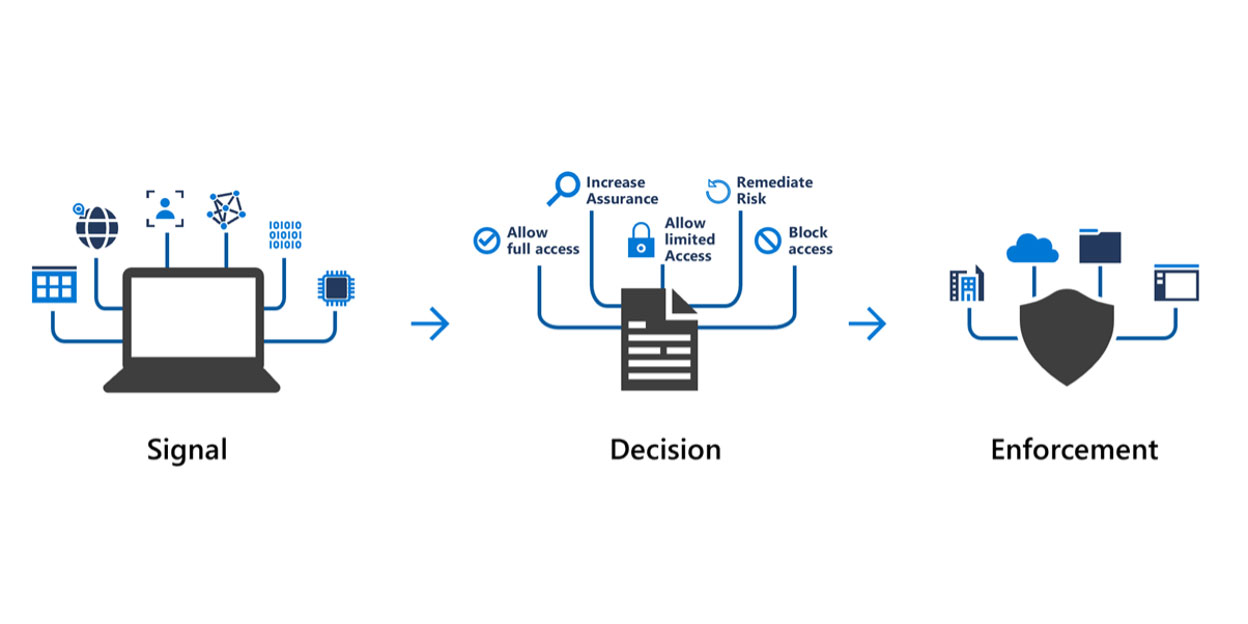
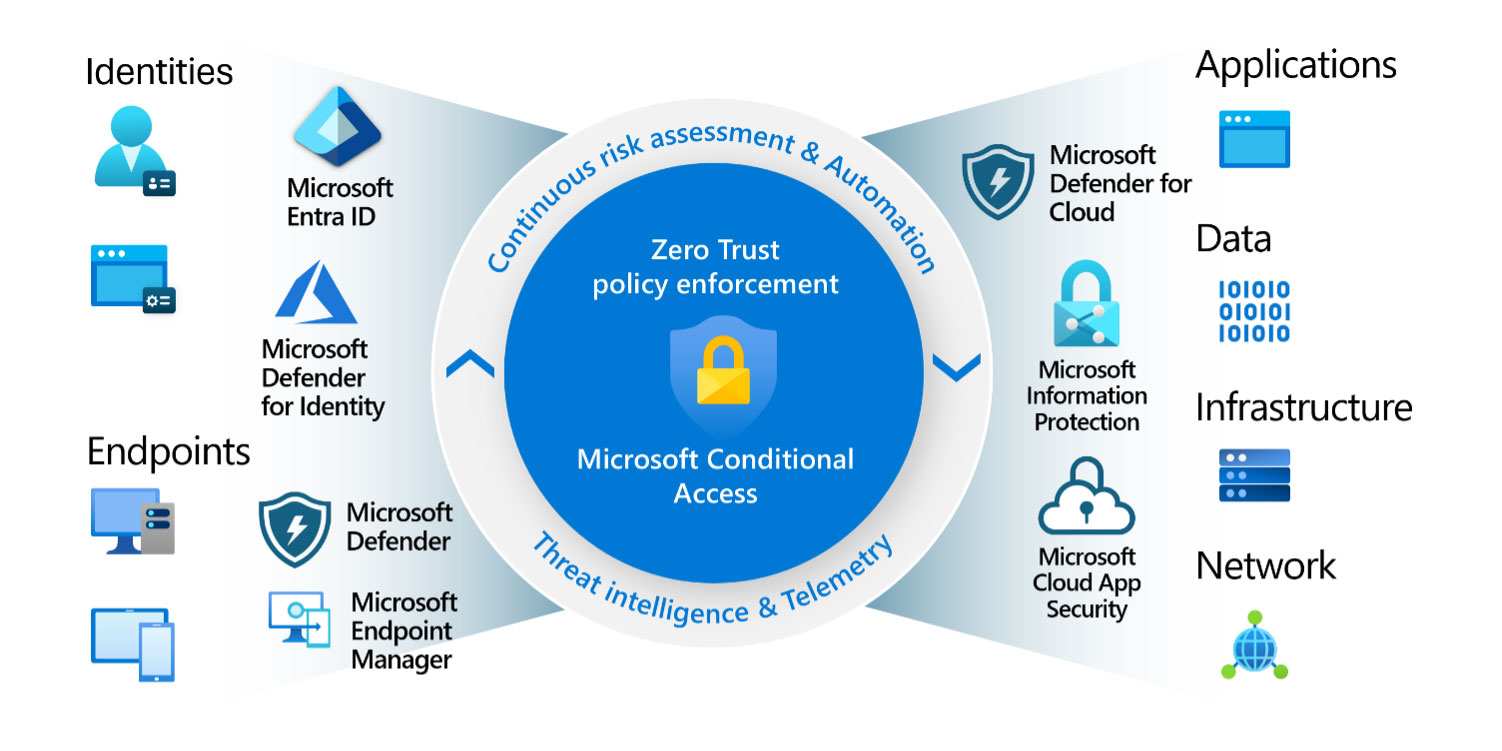
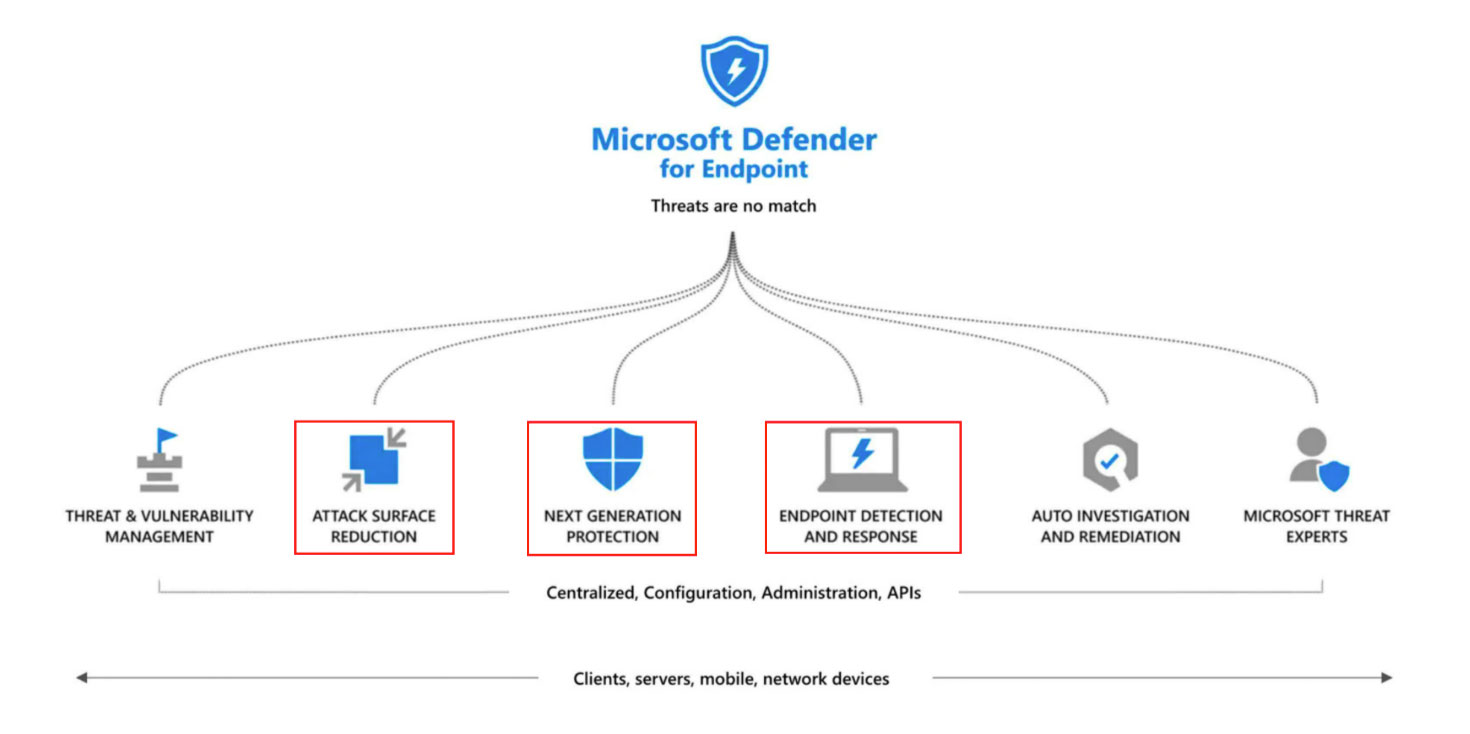
As previously mentioned, a successful DLP implementation program should cover all 3 main data exfiltration channels which are Web, Collaboration and Endpoint with all their subcomponents. When it comes to endpoints, onboarding Windows workstations to Purview is quite easy. If your organization provides MacOS devices to your users, these devices should also be onboarded to…