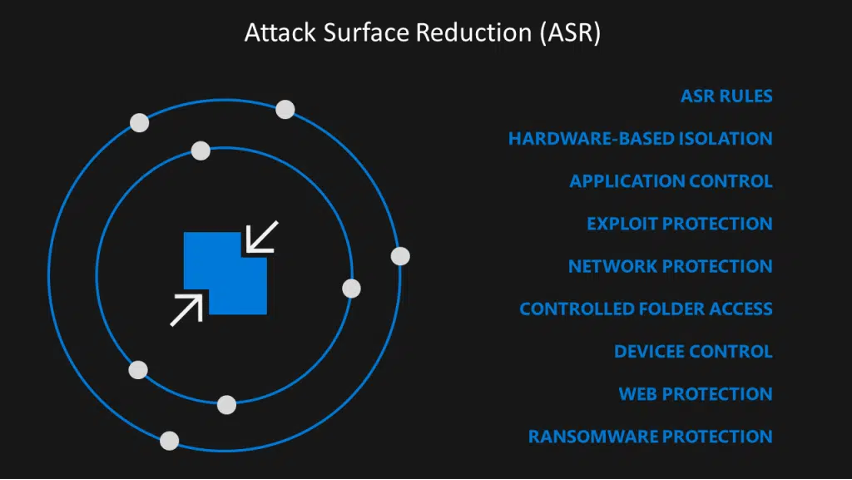
What is ASR?
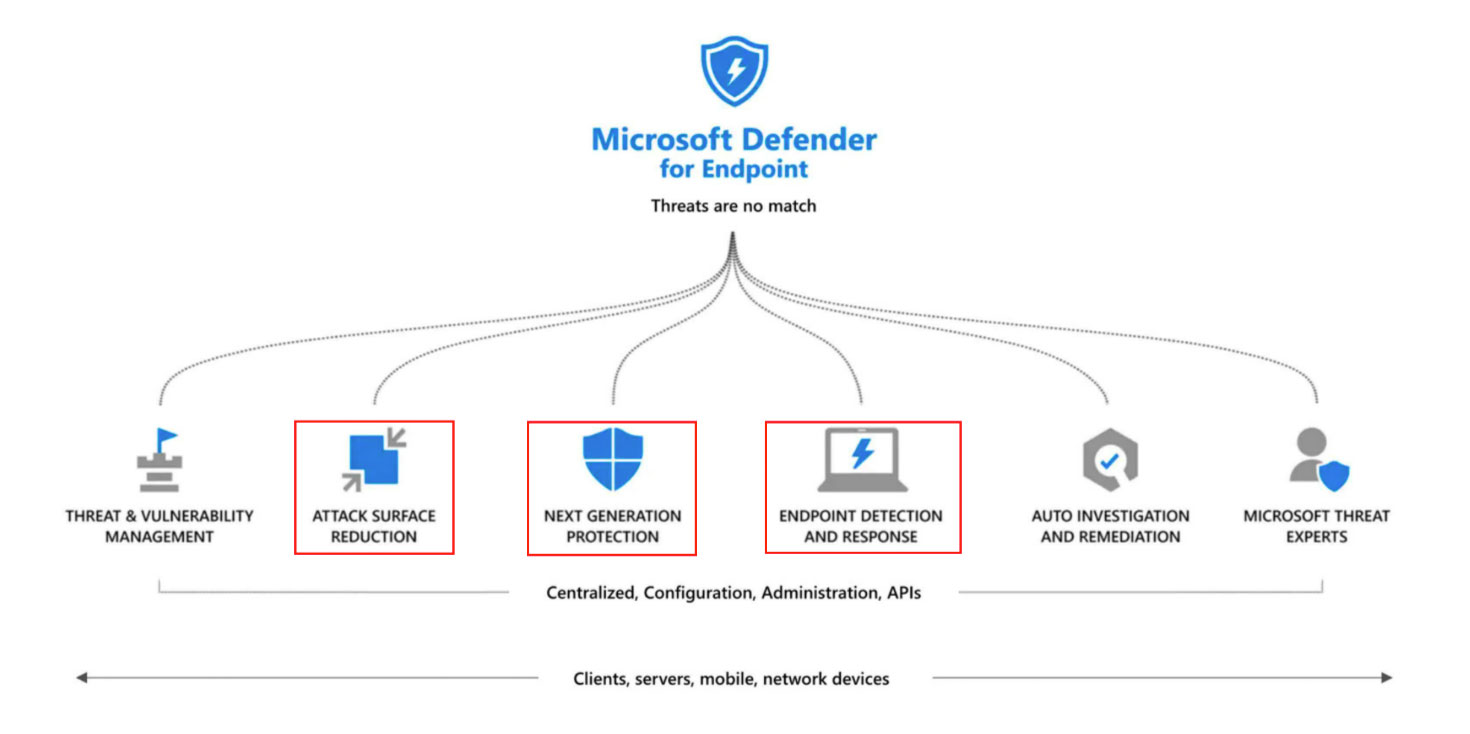
One of the capabilities of Microsoft Defender for Endpoint that is often overlooked because of its fancy name and fear of breaking things is Attack Surface Reduction also known as ASR.
The name of the feature is a little bit too big for what it achieves so far but is certainly a particularly useful feature. What it does is, it targets software behaviors that are often abused by attackers, such as:
- Launching executable files and scripts that attempt to download or run files.
- Running obfuscated or otherwise suspicious scripts
- Performing behaviors that apps do not usually initiate during normal day-to-day work.
Such behaviors are sometimes seen in legitimate applications; however, they are considered risky because they are commonly abused by malware. Attack surface reduction rules can constrain these kinds of risky behaviors and help keep your organization safe.
By preventing these usual suspects, an organization saves a lot of effort that can be spent in responding to security incidents in which one or more of these activities are used.
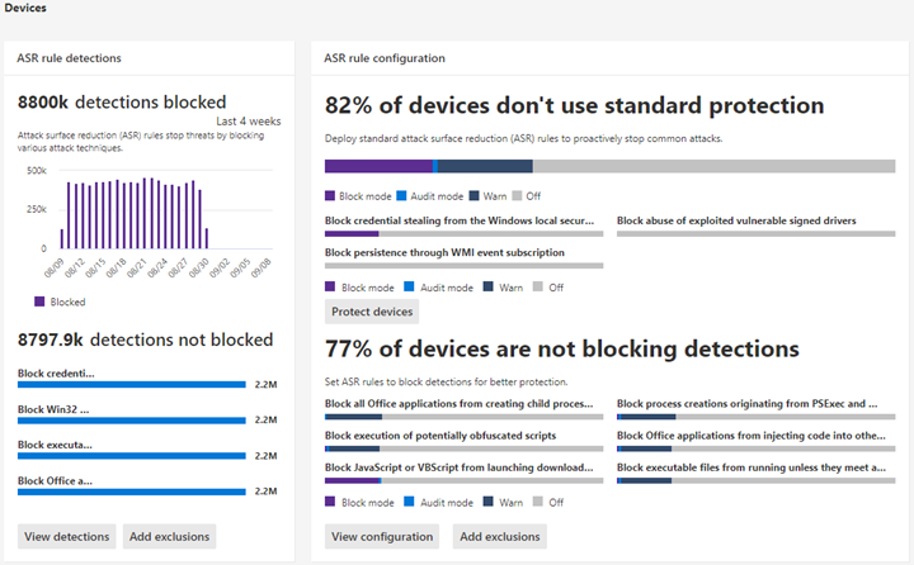
You can find the ASR rule (activity types) in the table below.
| Category | Rule name | GUID | File & folder exclusions |
| E-mail and Webmail | Block executable content from email client and webmail | BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550 | Supported |
| Microsoft Office | Block all Office applications from creating child processes | D4F940AB-401B-4EFC-AADC-AD5F3C50688A | Supported |
| Microsoft Office | Block Office applications from creating executable content | 3B576869-A4EC-4529-8536-B80A7769E899 | Supported |
| Microsoft Office | Block Office communication application from creating child processes | 26190899-1602-49e8-8b27-eb1d0a1ce869 | Supported |
| Microsoft Office | Block Win32 API calls from Office macros | 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B | Supported |
| Microsoft Office | Block Office applications from injecting code into other processes | 75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84 | Supported |
| Executables and Scripts | Block JavaScript or VBScript from launching downloaded executable content | D3E037E1-3EB8-44C8-A917-57927947596D | Not supported |
| Executables and Scripts | Block execution of potentially obfuscated scripts | 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC | Supported |
| Executables and Scripts | Block executable files from running unless they meet a prevalence, age, or trusted list criterion | 01443614-cd74-433a-b99e-2ecdc07bfc25 | Supported |
| Executables and Scripts | Use advanced protection against ransomware | c1db55ab-c21a-4637-bb3f-a12568109d35 | Supported |
| Block abuse of exploited vulnerable signed drivers | 56a863a9-875e-4185-98a7-b882c64b5ce5 | ||
| Windows Credentials | Block persistence through WMI event subscription | e6db77e5-3df2-4cf1-b95a-636979351e5b | Not supported |
| Windows Credentials | Block credential stealing from the Windows local security authority subsystem (lsass.exe) | 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 | Supported |
| Windows Management Interface (WMI) | Block process creations originating from PSExec and WMI commands | d1e49aac-8f56-4280-b9ba-993a6d77406c | Supported |
| Windows Management Interface (WMI) | Block persistence through WMI event subscription | e6db77e5-3df2-4cf1-b95a-636979351e5b | Not supported |
| Windows Management Interface (WMI) | Note: This setting is not yet available in MEM/MEMCM. | ||
| Device Control | Block untrusted and unsigned processes that run from USB | b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4 | Supported |
| 3rd Party Apps | Block Adobe Reader from creating child processes | 7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c | Supported |
Although some of these behaviors might be legitimate for some applications to work, they are considered risky as they are primarily used by attackers to carry on their attacks. Before enabling ASR rules in block-mode, you must run the rules in audit mode to capture more data and understand their impact on your business applications.
ASR rules are not about trusting or not trusting certain apps in your endpoints. They are about recognizing potentially malicious behaviors and minimizing the probability of an attacker using these behaviors to carry on an attack thus minimizing the overall risk level.
Requirement and Prerequisites
You can configure attack surface reduction rules for devices running any of the following editions and versions of Windows:
- Windows 10 Pro/Enterprise/Education, version 1709 or later.
- Windows Server, version 1803 (Semi-Annual Channel) or later.
- Windows Server 2019.
With Windows 10 Pro, you get the ASR rule capabilities. However, Windows 10 Enterprise E3 license gives you the entire feature-set of ASR rules, and you can use Event viewer to review attack surface reduction rule events.
While using event viewer might work for you, having the Windows E5 license with Microsoft Defender for Endpoint adds management and reporting layer for the ASR rules, such as monitoring, analytics, and workflow as part of Microsoft Defender for Endpoint.
In fact, Microsoft Defender for Endpoint takes ASR rules to the next level by onboarding those ASR rule events within the Microsoft 365 Defender portal.
Regardless of the license of choice, Microsoft Defender Antivirus must be active mode because ASR uses Microsoft Defender Antivirus to block the attempts.
This should be taken into consideration especially when you are using a third-party antivirus solution. In this case, the built-in Microsoft Defender Antivirus automatically goes into passive mode.
Finally, some ASR rules require the Microsoft Defender Antivirus cloud-delivered protection to be enabled.
Rule Exclusions
There are certainly going to be cases where a benign process will be identified as malicious, and you will have to define some exclusions to avoid the alert fatigue. This means that the ASR rule will ignore the execution of certain processes. For these cases, keep in mind the following:
- If you add an exclusion, it will affect every ASR rule. The reason for this is for performance and reliability (you cannot specify what ASR rule to exclude)
- Not all rules support exclusions.
- Excluded files/folders and processes will be allowed to run, and no report or event will be recorded.
- ASR rules exclusions are managed separately from Microsoft Defender Antivirus exclusions.
- ASR rules exclusions support wildcards, paths, and environmental variables. This is, however, only supported if you use Microsoft Intune. If you manage ASR rules through SCCM, you cannot use wildcards.
- Wildcards cannot be used to define a drive letter.
- ASR rules exclusions are not user context aware (ASR rules run under NT AUTHORITY\SYSTEM account), so it is not possible to add user profile folder to exclusions using environmental variables such as %USERPROFILE%.
Configuring ASR Rules
There are four states for any ASR rule:
- Not configured: which means disabled.
- Block: Block and log the identified suspicious activity attempts.
- Audit: Detect and log the activity but not block.
- Warn: Enforce the rules but provide the users with a possibility to override the block action for 24 hours. This allows you to test rules, without necessarily blocking your end-users.
The warn mode is available for all rules except:
- Block JavaScript or VBScript from launching downloaded executable content.
- Block persistence through WMI event subscription.
- Use advanced protection against ransomware.
You do not have to enable all ASR rules at once. Many business applications were written with limited security concerns, and they might perform tasks that resemble malware or malicious activity.
A recommended approach is to enable ASR rules in audit mode first to better understand the impact of enabling each of these rules. By monitoring audit data and adding exclusions for necessary applications, you can deploy ASR rules without impacting productivity.
It is worth mentioning that dealing with Office macros is difficult for security professionals. They represent an effortless way for attackers to launch their attacks. Unfortunately, many customers still depend on Office macros to run their businesses. Special attention might be required for enforcing the related rule in block mode.
The warn mode is available for all rules except:
- Block JavaScript or VBScript from launching downloaded executable content.
- Block persistence through WMI event subscription.
- Use advanced protection against.
You can configure ASR rules using one of the following methods:
- Microsoft Intune
- 3rd-party Mobile Device Management (MDM)
- Microsoft Endpoint Configuration Manager
- Group Policy
- PowerShell
We are ready to help you deploy MDE’s ASR capabilities for your organization using your tool of choice. Please contact us to learn more about it.