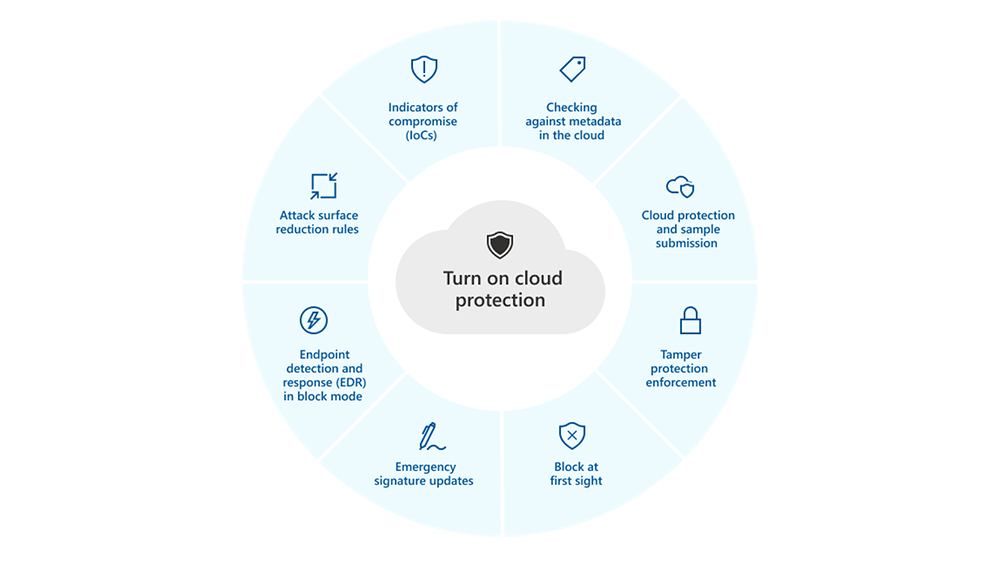
Why Customizing Microsoft Defender for Endpoint Antivirus Policy Settings is Crucial
Microsoft Defender for Endpoint (MDE)is a powerful endpoint security solution that provides advanced threat protection and response capabilities. While the default settings offer a good baseline of protection, customizing these settings to align with your organization’s specific needs is crucial. Here’s why adjusting the antivirus policy settings in MDE is important for your organization’s security and performance:
Tailored Threat Protection
Targeted Threats: Every organization faces unique threats depending on its industry, location, and size. Customizing antivirus policies helps defend against specific threats that are more likely to target your organization.
Advanced Threat Detection: Fine-tuning the settings allows for more effective use of advanced detection techniques, enhancing overall threat detection capabilities.
Optimized Performance
Resource Management: Default settings might not be optimized for your specific hardware and network configuration. Customizing settings ensures that the antivirus software does not unnecessarily consume resources, maintaining optimal system performance.
Minimized Business Disruption: Adjusting scan schedules and intensity can reduce the impact on users’ productivity by ensuring that resource-intensive scans are performed during off-peak hours.
Improved Incident Response
Customized Alerting: Configuring custom alert thresholds and notification settings ensures that critical alerts are prioritized and addressed promptly, reducing the response time to potential security incidents.
Automatic Remediation: Custom policies can enable or adjust automatic remediation actions based on the severity of threats, ensuring swift containment and resolution of incidents.
Inclusion of Critical Areas: Conversely, you can specify critical areas of your infrastructure that require more stringent scanning and protection, ensuring that high-risk assets are thoroughly protected.
Key Areas to Customize in Antivirus Policy Settings
Scan Settings: Adjust the frequency, depth, and timing of scans to balance protection and performance. This includes configuring quick scans, full scans, and scheduled scans according to organizational needs.
Real-Time Protection: Fine-tune real-time protection settings to ensure immediate detection and mitigation of threats without significantly impacting system performance.
Cloud Delivered Protection: Enable or adjust cloud-delivered protection settings to leverage the latest threat intelligence and provide rapid response to new threats.
Automatic Sample Submission: Configure settings for automatic sample submission to Microsoft for analysis, helping improve detection rates and reduce false positives.
Remediation Actions: Customize the remediation actions that should be taken for different types of threats, including automatic quarantine, removal, or user notification.
You can find below 3 different MDE Antivirus Policies in detail, with all the important settings configured for general use Windows Endpoints (Windows 10 and 11) as well as for general purpose and mission critical Windows Servers.
| Setting | Configuration Options | Workstations | Servers | Mission Critical Servers | Explanation |
|---|---|---|---|---|---|
| Allow Archive Scanning | Not Allowed Allowed Not configured | Allowed | Allowed | Not Allowed | This policy setting allows you to configure scans for malicious software and unwanted software in archive files such as . ZIP or . CAB files. If you have servers with lots of archived documents, this setting might make the scans run for too long and consume too much resources. Group such servers together to exclude them from this policy setting. |
| Allow Behavior Monitoring | Not Allowed Allowed Not configured | Allowed. | Allowed | Allowed | This policy setting allows you to configure behavior monitoring. If you enable or don’t configure this setting, behavior monitoring will be enabled. |
| Allow Cloud Protection | Not Allowed Allowed Not configured | Allowed | Allowed | Allowed | Certain security features and capabilities in Microsoft Defender for Endpoint only work when cloud protection is enabled. |
| Allow Email Scanning | Not Allowed Allowed Not configured | Allowed | Not Allowed | Not Allowed | This policy setting allows you to configure e-mail scanning. When e-mail scanning is enabled, the engine will parse the mailbox and mail files to analyze the mail bodies and attachments. E-mail reception is not an activity that is expected to happen on servers. Unless your application receives and processes emails as part of a business integration do not activate this policy setting on servers. |
| Allow Full Scan On Mapped Network Drives | Not Allowed Allowed Not configured | Not Allowed | Not Allowed | Not Allowed | The scans take much longer on machines and it is not logical to scanned mapped drives from every single computer. File Servers hosting the files should be scanned instead of activating this feature. |
| Allow scanning of all downloaded files and attachments | Not Allowed Allowed Not configured | Allowed | Allowed | Allowed | |
| Allow Realtime Monitoring | Not Allowed Allowed Not configured | Allowed | Allowed | Allowed | Allows or disallows Windows Defender Realtime Monitoring functionality. |
| Allow Scanning Network Files | Not Allowed Allowed Not configured | Allowed | Allowed | Allowed | This policy setting allows you to configure scheduled scans and on-demand (manually initiated) scans for files that are accessed over the network. It is recommended to enable this setting. |
| Allow Script Scanning | Not Allowed Allowed Not configured | Allowed | Allowed | Allowed | |
| Avg CPU Load Factor | Not Configured Configured | Configured. 50 | Configured. 30 | Configured.20 | This policy setting allows you to configure the maximum percentage CPU utilization permitted during a scan. Valid values for this setting are a percentage represented by the integers 5 to 100. A value of 0 indicates that there should be no throttling of CPU utilization. The default value is 50. If you enable this setting, CPU utilization won’t exceed the percentage specified. If you disable or don’t configure this setting, CPU utilization won’t exceed the default value. |
| Cloud Block Level | Default State High High Plus Zero Tolerance Not Configured | High | High | High | This policy setting determines how aggressive Microsoft Defender Antivirus will be in blocking and scanning suspicious files. Moderate- Microsoft Defender Antivirus blocking level, delivers verdict only for high confidence detections High- aggressively block unknowns while optimizing client performance (greater chance of false positives) High+ – aggressively block unknowns and apply additional protection measures (may impact client performance) Zero tolerance – block all unknown executables. |
| Cloud Extended Timeout | Not Configured Configured | Configured. 50 | Configured. 20 | Configured. 20 | This feature allows Microsoft Defender Antivirus to block a suspicious file for up to 60 seconds, and scan it in the cloud to make sure it’s safe. The typical cloud check timeout is 10 seconds. To enable the extended cloud check feature, specify the extended time in seconds, up to an additional 50 seconds. Be extremely careful applying this setting on servers where too many new documents are being ingested |
| Disable Catchup Full Scan | Disabled Enabled Not Configured | Enabled | Disabled | Disabled | This policy setting allows you to configure catch-up scans for scheduled full scans. A catch-up scan is a scan that’s initiated because a regularly scheduled scan was missed. Usually these scheduled scans are missed because the computer was turned off. Full scans for Servers should only happen on specific times where maintenance activities are permitted and off-peak periods, hence the Disabled setting recommendation. |
| Disable Catchup Quick Scan | Disabled Enabled Not Configured | Enabled | Enabled | Enabled | This policy setting allows you to configure catch-up scans for scheduled quick scans. A catch-up scan is a scan that’s initiated because a regularly scheduled scan was missed. Usually these scheduled scans are missed because the computer was turned off at the scheduled time. Quick scans are not resource intensive and very often take only a couple of minutes. It is recommended to enable this setting for all systems. |
| Enable Low CPU Priority | Disabled Enabled Not Configured | Enabled | Enabled | Enabled | |
| Enable Network Protection | Disabled Enabled (Audit Mode) Enabled (Block Mode) Not Configured | Enabled (block mode) | Enabled (block mode) | Enabled (block mode) | Enable or disable Microsoft Defender Exploit Guard network protection to prevent employees from using any application to access dangerous domains that may host phishing scams, exploit-hosting sites, and other malicious content on the Internet. Enabled-Block: Users and applications won’t be able to access dangerous domains Enabled-Audit Mode: Users and applications can connect to dangerous domains, however if this feature would’ve blocked access if it were set to Block, then a record of the event will be in the event logs. Disabled: Users and applications won’t be blocked from connecting to dangerous domains. Not configured: Same as Disabled. |
| PUA Protection | PUA Protection off. PUA Protection on Not Configured | PUA protection on | Audit Mode | Audit Mode | PUA Protection off. Windows Defender will not protect against potentially unwanted applications PUA Protection on. Detected items are blocked. They will show in history along with other threats. Audit mode. Windows Defender will detect potentially unwanted applications, but take not action. |
| Real Time Scan Direction | Monitor incoming files. Monitor outgoing files. Monitor all files (bi-directional). Not Configured | Monitor all files (bi-directional). | Monitor all files (bi-directional). | Monitor all files (bi-directional). | |
| Scan Parameter | Quick Scan Full Scan Not Configured | Quick scan | Quick scan | Quick scan | These options configure regular scans to happen every Monday at 12:00 PM (720 minutes after midnight). Please change these settings for your organization accordingly. Think also about creating different groups of servers for reduced impact on servers. |
| Schedule Quick Scan Time | Not Configured Configured | Configured. 720 | Configured. 720 | Configured. 720 | |
| Schedule Scan Day | Days (…) Not Configured | Monday | Monday | Monday | |
| Signature Update Interval | Not Configured Configured | Configured. 8 | Configured. 2 | Configured. 2 | This policy setting allows you to specify an interval at which to check for security intelligence updates. The time value is represented as the number of hours between update checks. Valid values range from 1 (every hour) to 24 (once per day). |
| Submit Samples Consent | Always prompt Send safe samples automatically Never send Send all samples automatically Not configured | Send all samples automatically | Never send | Never send | This policy setting configures behavior of samples submission when opt-in for MAPS telemetry is set. |
| Allow On Access Protection | Allowed Not allowed Not configured | Allowed | Allowed | Allowed | |
| Remediation action for Severe Threats | Clean. Quarantine. Removed. Allow User defined Not configured | Block | Block | Block | Clean. Service tries to recover files and try to disinfect. Quarantine. Moves files to quarantine Removed. Removes files from system. Allow. Allows file/does none of the above actions. User defined. Requires user to make a decision on which action to take. Not configured |
| Remediation action for Moderate Threats | Quarantine | Quarantine | Quarantine | ||
| Remediation action for Low Threats | Clean | Clean | Clean | ||
| Remediation action for HighThreats | Block | Block | Block | ||
| Allow Network Protection Down Level | Network protection will be disabled downlevel. Network protection will be enabled downlevel. Not configured | Network protection will be enabled downlevel. | Network protection will be enabled downlevel. | Network protection will be enabled downlevel. | Down Level means older version operating systems. Network Protection needs to be enabled on all endpoints. |
| Engine Updates Channel | Not configured. Beta Channel Current Channel(Preview) Current Channel(Staged) Current Channel(Broad) Critical – Time delay | Current Channel(Broad) | Current Channel(Broad) | Critical – Time delay | See detailed explanation in the below table. |
| Platform Updates Channel | Not configured. Beta Channel Current Channel(Preview) Current Channel(Staged) Current Channel(Broad) Critical – Time delay | Current Channel(Broad) | Current Channel(Broad) | Critical – Time delay | See detailed explanation in the below table. |
| Security Intelligence Updates Channel | Not configured. Beta Channel Current Channel(Preview) Current Channel(Staged) Current Channel(Broad) Critical – Time delay | Current Channel(Broad) | Current Channel(Broad) | Current Channel(Broad) | See detailed explanation in the below table. |