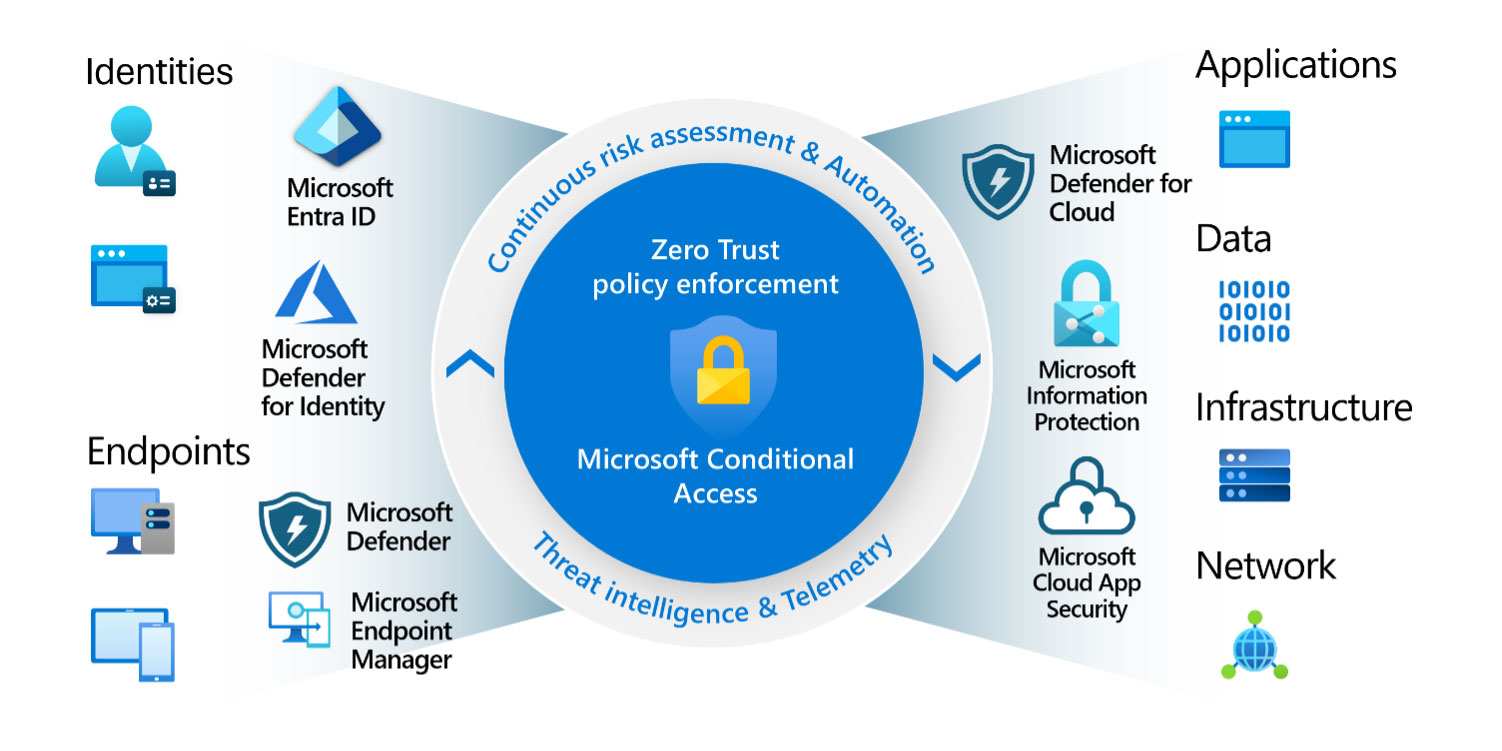
Introduction to Conditional Access
More and more applications are made available to the users on public internet with organizations embracing Microsoft’s Defender applications and the Azure platform. Many organizations and their administrators are unaware of what they expose to the Internet by following the routine configuration steps.
Conditional Access is a powerful feature offered by Microsoft that enables organizations to define and enforce access policies for their apps and resources. It analyzes signals such as user, device, and location to automate decisions and enforce access controls based on organizational policies. By implementing Conditional Access, businesses can adopt a Zero Trust security posture, ensuring that access is granted only to authorized users under specific conditions.
Planning a Conditional Access deployment requires careful consideration and strategy to ensure effective and secure access controls. In this comprehensive guide, we will explore the key aspects of planning a Conditional Access deployment and provide practical insights for a successful implementation.
Understanding Conditional Access Policies
Conditional Access Policies allow organizations to define the conditions under which access should be granted, limited, or blocked. By building conditional statements, businesses can tailor access controls based on user attributes, device compliance, location, and other factors.
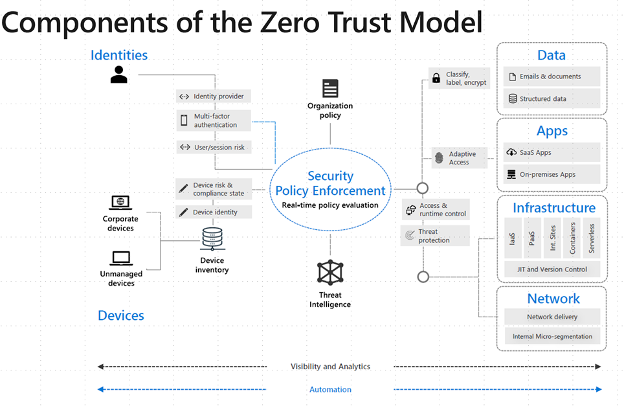
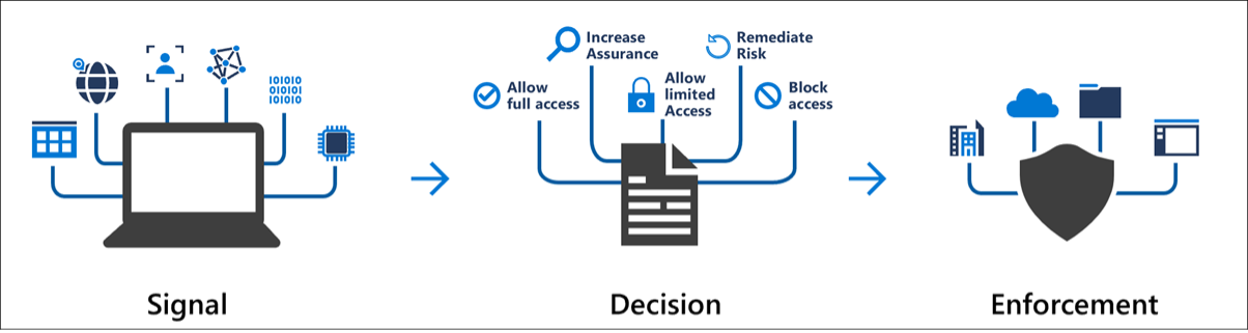
A Conditional Access policy consists of 3 major categories of components that work together to enforce access controls. These categories are:
1. Signals (Policy Conditions)
- Users: Organizations can define which users, groups, directory roles, or workload identities are included or excluded from the policy. Additionally, emergency access accounts and service accounts should be carefully managed and excluded from policies to prevent locking down your administrators’ access.
- Devices
- Network Locations
- User Risk
- Sign-in Risk
2. Decision (Policy Controls)
- Allow Access
- Require MFA
- Deny Access
- Require Password Reset
- Apply Session Controls
3. Enforcement (Applications)
Conditional Access policies can be applied to specific cloud applications, user actions, or authentication contexts. Organizations can specify which applications the policy applies to.
Prerequisites for Conditional Access Deployment
Before deploying Conditional Access policies, organizations must ensure they meet the necessary prerequisites. This includes having:
- Microsoft Entra ID P2 licenses.
- Relevant role assignments (Conditional Access Administrator or Security Administrator) for Conditional Access administrators.
- Test user groups to verify policy functionality.
Designing Conditional Access Policies
Designing effective Conditional Access policies can be complex and require some getting used to. They are however critical to protect your organizations critical assets such as Azure Platform Management, Microsoft Admin Portals among other things.
At this point, we recommend a 2 phased approach. In the first phase, the Conditional Access Policies that are recommended by Microsoft and tested by many organizations should be deployed. The first phase policies are low risk, but they are important to be in line with your organization’s security policies and compliance requirements.
The second phase addresses your organization’s specific needs, like creating more fined tuned policies taking into consideration the applications specific contexts.
Before going into the detail of starting the phased deployment, recommendations given below must be followed.
1. Minimize the Number of Conditional Access Policies
Creating a separate policy for each app can be inefficient and challenging to manage. Conditional Access has a limit of 195 policies per-tenant, so it’s advisable to analyze apps and group them based on resource requirements for similar users. By creating a single policy for multiple apps with similar requirements, you can minimize policy complexity and administration efforts.
2. Configure Report-Only Mode for Testing
By default, Conditional Access policies are created in report-only mode. Organizations should evaluate the effect of policies using report-only mode, simulate real-time sign-ins, and use tools like the Conditional Access insights and Reporting workbook to validate the intended results.
3. Plan for Disruptions and Resilience
Relying on a single access control for security can be risky. Organizations should plan for resilience strategies in case of access failures or disruptions. This may involve implementing backup access controls, such as temporary emergency policies, to ensure continuous access during unforeseen circumstances.
4. Block Unauthorized Countries/Regions
To enhance security, organizations can utilize Conditional Access named locations to block countries or regions from which they never expect sign-ins. By creating a network block policy that excludes allowed countries/regions, organizations can minimize the overhead of managing access from smaller geographic locations.
Deploying and Troubleshooting Conditional Access Policies
Once policies are designed and tested, organizations can proceed with deploying Conditional Access policies in production. This involves building policies based on templates and recommendations, evaluating policy impact, and gradually enabling policies in report-only mode. Care should be taken to monitor the effect of policies using sign-in logs and tools like the What-If tool. Policies can be enabled once their impact has been confirmed, and administrators should also be familiar with rollback options.
For troubleshooting, administrators can identify and resolve problems related to Conditional Access policies by using resources like sign-in logs and error messages. The What-If tool can also be useful in evaluating policy application in specific circumstances.
Conclusion
Planning a Conditional Access deployment is a critical step in ensuring secure access to apps and resources. By carefully designing policies, considering user and workload identities, and leveraging the flexibility of Conditional Access, organizations can achieve a robust access control framework. With the recommendations and best practices outlined in this guide, businesses can navigate the complexities of Conditional Access deployment and enhance their overall security posture.
You can find more detail about the Deployment of 10 Essential Conditional Access Policies in our next blog article.