Locking Down Your Cloud: Essential Service Control Policies for Robust AWS Security
The need for ensuring the safety and compliance of AWS environments is paramount for organizations that have a large footprint in AWS with tens of accounts and environments to manage. AWS Organizations offers Service Control Policies (SCPs) – a powerful tool to establish security guardrails across your entire organization. This blog dives into the most essential SCPs you should implement for robust AWS security.
Why Use SCPs?
SCPs act as guardrails, defining permissions for actions users can take within your AWS accounts. These policies are attached to Organizational Units (OUs) within your AWS Organization structure, inheriting down to all accounts within that OU. This centralized approach ensures consistent security configurations across your entire environment.
Here’s why SCPs are crucial:
- Centralized Control:Manage security policies from a single point, streamlining administration and reducing inconsistencies.
- Privilege Governance:Enforce limitations on IAM permissions, preventing privilege escalation and unauthorized access.
- Compliance Adherence:Align your AWS environment with security regulations and internal security standards.
- Security Automation:Automate security best practices, reducing manual configuration and human error.
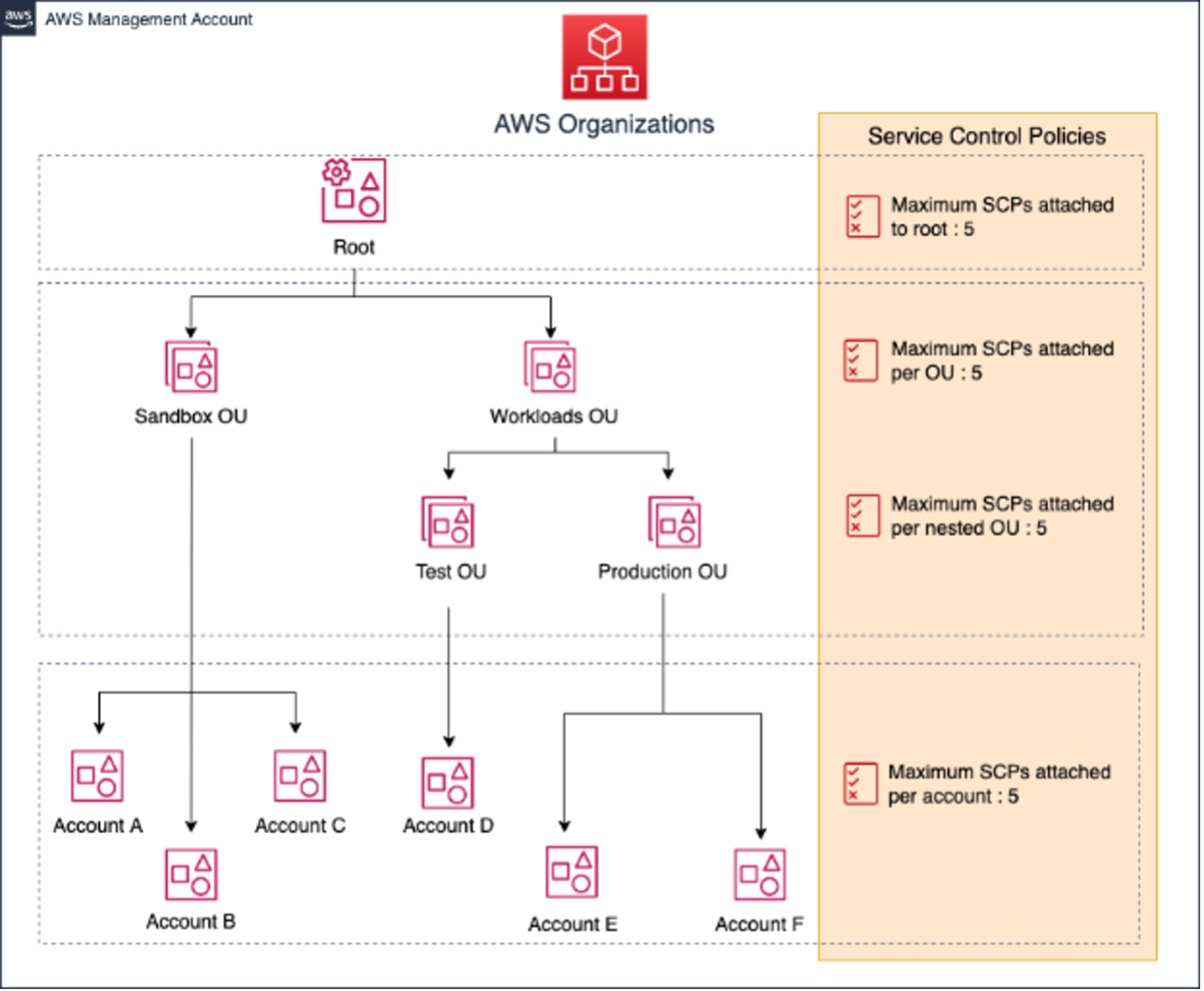
Essential SCPs for Your AWS Organization
Here are some of the most critical SCPs to implement for a secure AWS environment:
- Protect Security Services:
Policy Focus: Prevent disabling critical security tools like Amazon GuardDuty, AWS Config, and AWS CloudTrail.
Security Benefit: Ensures these services remain active to detect and respond to threats.
Consider an SCP like this:
JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Principal”: “*”,
“Action”: [
“guardduty:DeleteDetector”,
“guardduty:StopMonitoringMembers”,
“config:DeleteDeliveryChannel”,
“config:StopConfigurationRecorder”,
“config:DeleteAggregationAuthorization”,
“cloudtrail:DeleteTrail”,
“cloudtrail:StopLogging”
],
“Resource”: “*”
}
]
}
}
}
]
}
- Control Public S3 Bucket Creation:
Policy Focus: Restrict creation of internet-facing resources like Amazon S3 buckets with public access.
Security Benefit: Mitigates accidental data exposure and unauthorized access.
An SCP like this enforces restrictions:
JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Principal”: “*”,
“Action”: [
“s3:CreateBucket”,
“s3:PutBucketAcl”
],
“Condition”: {
“StringEquals”: {
“s3:PublicAccess”: “true”
}
}
}
]
}
- Enforce Encryption on S3 Buckets
Policy Focus: Enforce encryption of S3 Buckets.
Security Benefit: Ensures that data stored in S3 Buckets is encrypted with an industry standard encryption algorithm.
Following SCP can help you enforce this control.
JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Action”: “s3:PutObject”,
“Resource”: “arn:aws:s3:*”,
“Condition”: {
“StringNotEquals”: {
“s3:x-amz-server-side-encryption”: “AES256”
}
}
}
]
}
This policy ensures that all objects put into the specified S3 bucket are encrypted with AES-256 encryption.
- Enforce MFA for Root Users:
Policy Focus: Mandate Multi-Factor Authentication (MFA) for root users.
Security Benefit: Adds an extra layer of security to prevent unauthorized access to the most privileged accounts.
An SCP can achieve this by denying access without MFA:
JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Principal”: {
“AWS”: “arn:aws:iam::*:root”
},
“Action”: “sts:GetSessionToken”,
“Condition”: {
“Bool”: “false”,
“aws:MultiFactorAuthAge”: “0”
}
}
]
}
- Limit IAM User Permissions:
Policy Focus: Set a maximum permission level for IAM users within your accounts.
Security Benefit: Reduces the attack surface by restricting users to the least privilege principle.
An SCP can enforce permission guardrails like this:
JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Principal”: “*”,
“Action”: [
“iam:CreateUser”,
“iam:PassRole”
],
“Condition”: {
“ForAllValues:StringLike”: {
“iam:PolicyDocument”: {
“Statement”: [
{
“Effect”: “Allow”,
“Action”: “*”,
“Resource”: “*”
}
]
}
}
}
}
]
}
- Prevent Users from Deleting VPC Flow Logs:
Policy Focus: Prevent VPC Flow Logs from getting deleted.
Security Benefit: VPC flow logs are important information for security analytics and must be retained for security and compliance reasons.
JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Action”: [
“ec2:DeleteFlowLogs”,
“logs:DeleteLogGroup”,
“logs:DeleteLogStream”
],
“Resource”: “*”
}
]
}
- Prevent Member Accounts from Leaving the Organization:
Policy Focus: Prevent the accidental leave of an AWS account from AWS Organizations structure.
Security Benefit: An AWS Account that is no longer part of an AWS Organizations structure loses the security controls that are applicable to the organization and becomes risky.
JSON
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Deny”,
“Action”: [
“organizations:LeaveOrganization”
],
“Resource”: “*”
}
]
}
Best Practices for SCP Implementation
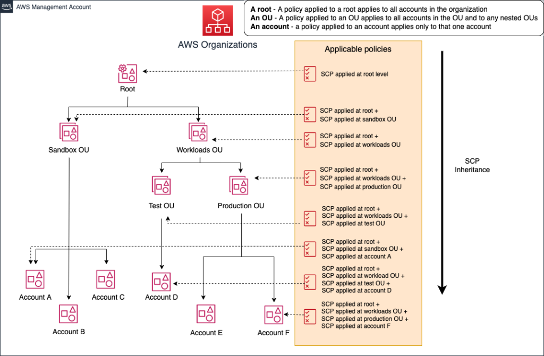
Start Simple: Begin with a foundational set of SCPs and gradually add more as needed.
Test Thoroughly: Use test accounts within a separate OU to validate SCP behavior before deployment.
Monitor Continuously: Utilize AWS CloudTrail to track SCP activity and identify any unexpected behavior.
Document Everything: Maintain clear documentation of your SCPs, including their purpose and effects.
Conclusion
SCPs are a powerful tool for securing your AWS multi-account environment. By implementing the essential SCPs outlined above, you can establish a strong security foundation, enforce compliance, and reduce the risk of misconfigurations and malicious activity. Remember, security is an ongoing process. Regularly review and update your SCPs to adapt to evolving threats and your organization’s security needs.
While these SCP policies are essential to be applied to ensure the security of your AWS estate, they should be applied with the utmost attention. A faulty policy can lock out your administrators or critical employees from carrying on their tasks for some time.
Having applied SCP Policies for many customers, we are here to help you safely apply these policies to your AWS environment and develop other custom SCP specific to your needs.
